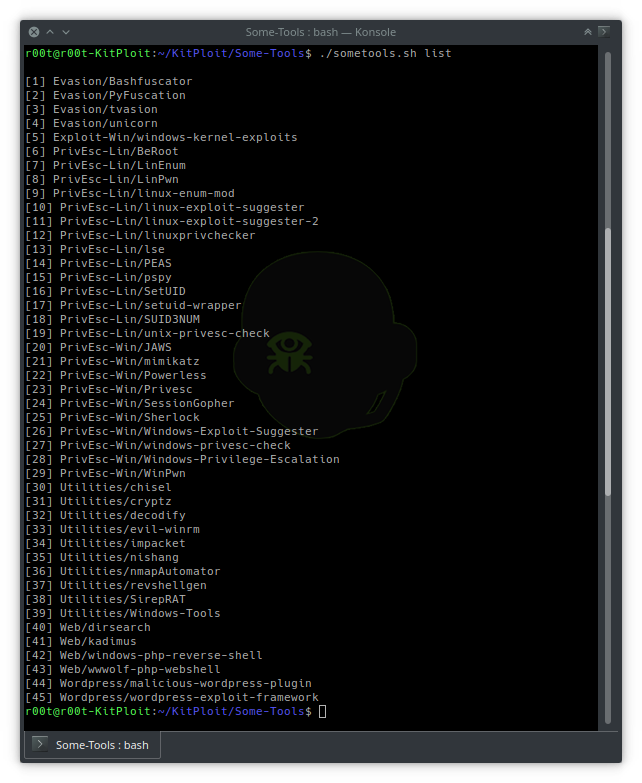
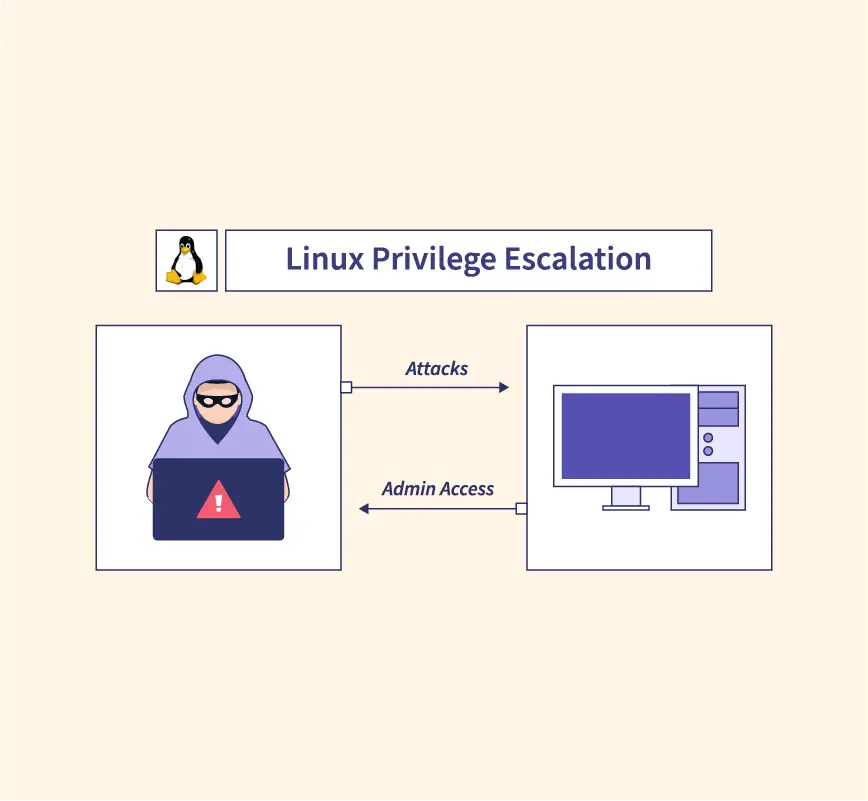
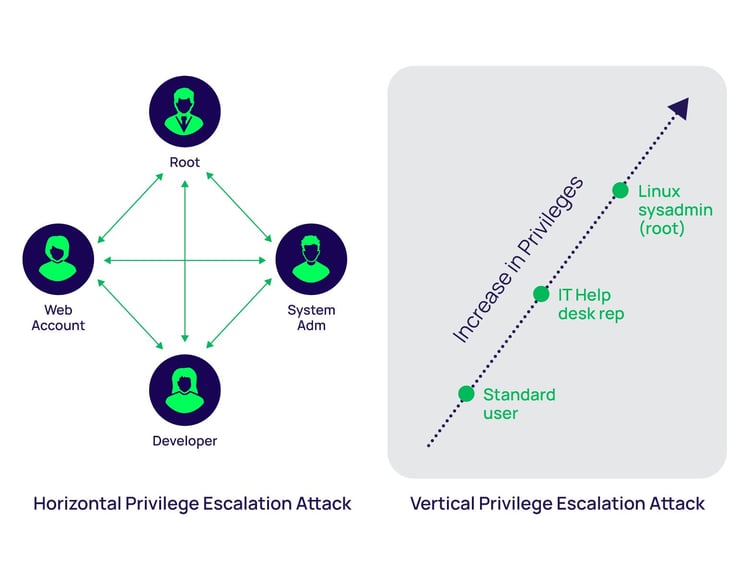
What Is A Privilege Escalation Attack? How To Prevent Privilege Escalation Attacks? - The Sec Master

Offensive Security Tool: PEASS (Privilege Escalation Awesome Scripts Suite) As Shell is the beginning, once a hacker accesses a system, which is not so... | By Black Hat Ethical HackingFacebook

THE CYBER GUY on Instagram: "Linux privilege escalation is the process of exploiting a vulnerability in a Linux system to gain access to privileges that are not normally available to a user.

Linux Exploit Suggester - Linux Privilege Escalation Auditing Tool - Kali Linux 2018.1 – PentestTools
![Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube](https://i.ytimg.com/vi/p-MoSi5WvIM/mqdefault.jpg)
Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube

TryHackMe — Jr Penetration Tester | Privilege Escalation | Linux Privesc | Part 2 | by Aditya Sharma | Medium
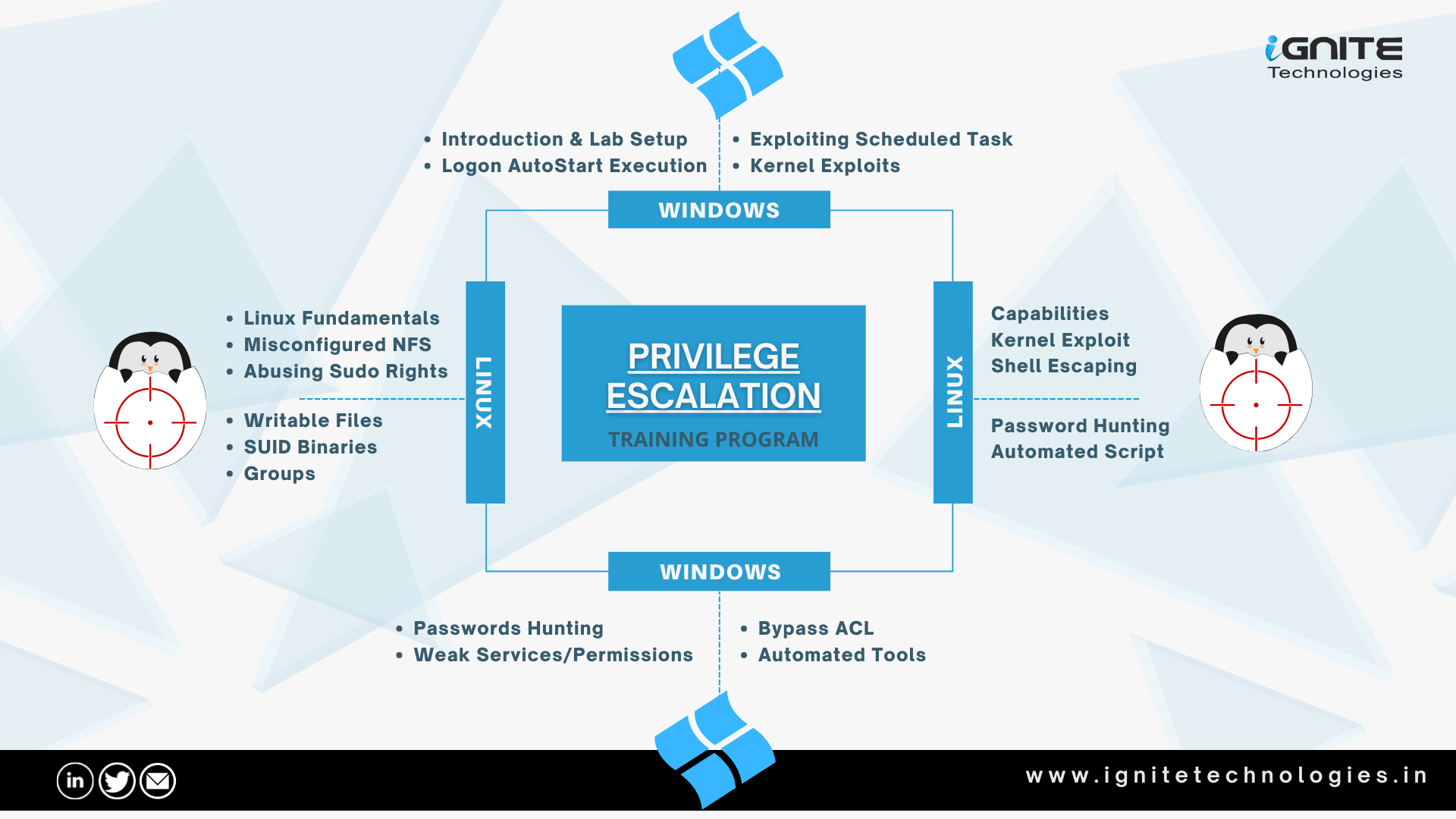
![Linux privilege checker - Advanced Infrastructure Penetration Testing [Book] Linux privilege checker - Advanced Infrastructure Penetration Testing [Book]](https://www.oreilly.com/api/v2/epubs/9781788624480/files/assets/0f21b2d6-ffb5-4181-b736-fc9d36a554da.png)
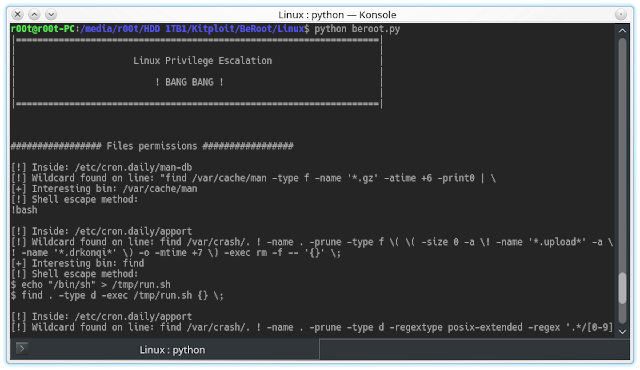

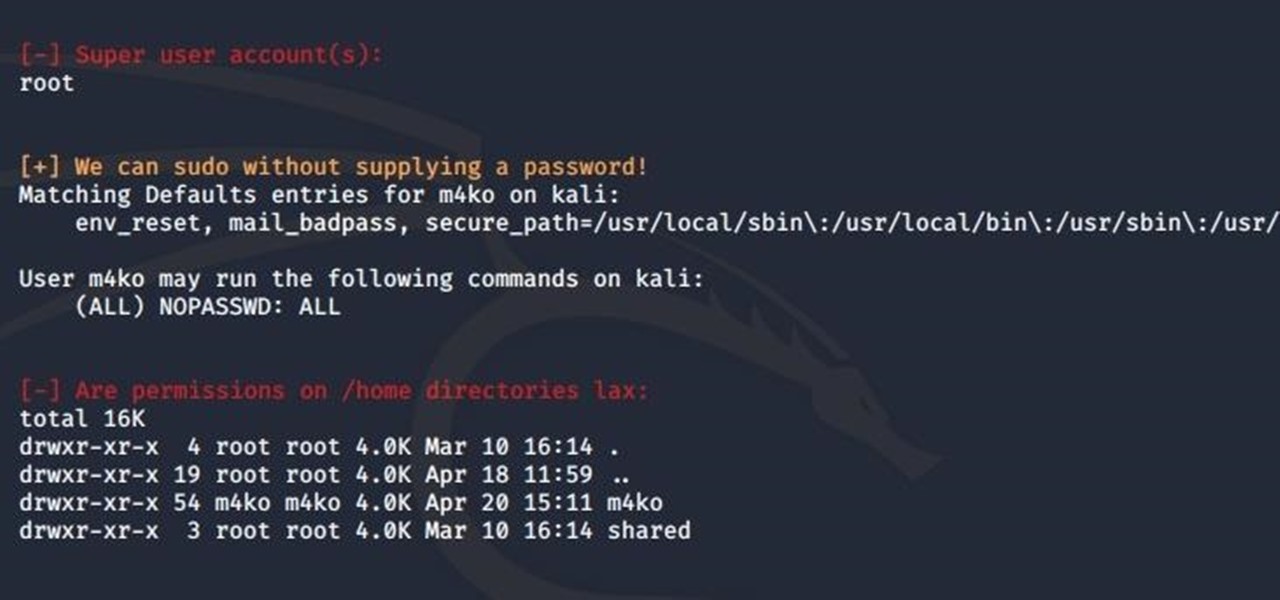

![Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux] - Yeah Hub Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2018/08/powershell-empire-priv-esc-setoolkit-2.png)