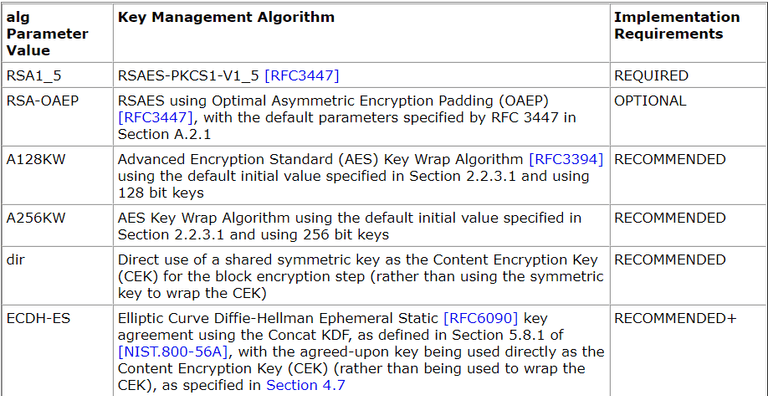
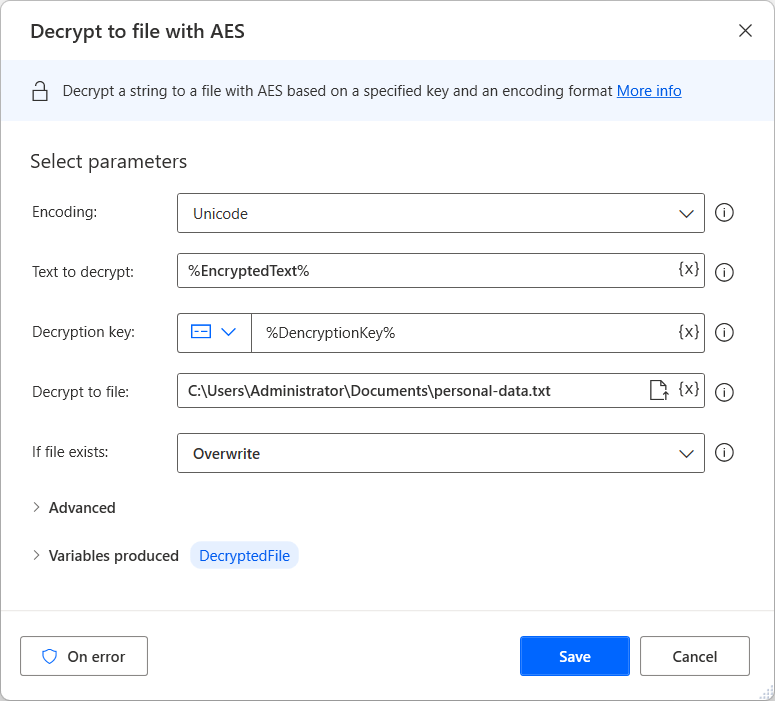
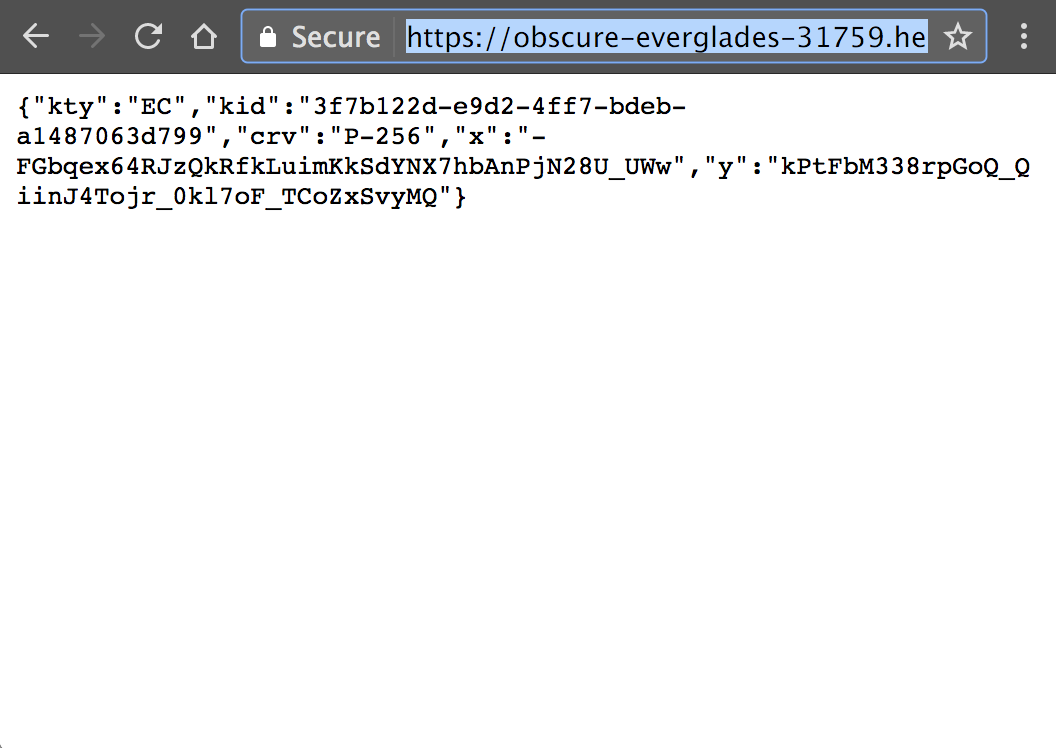
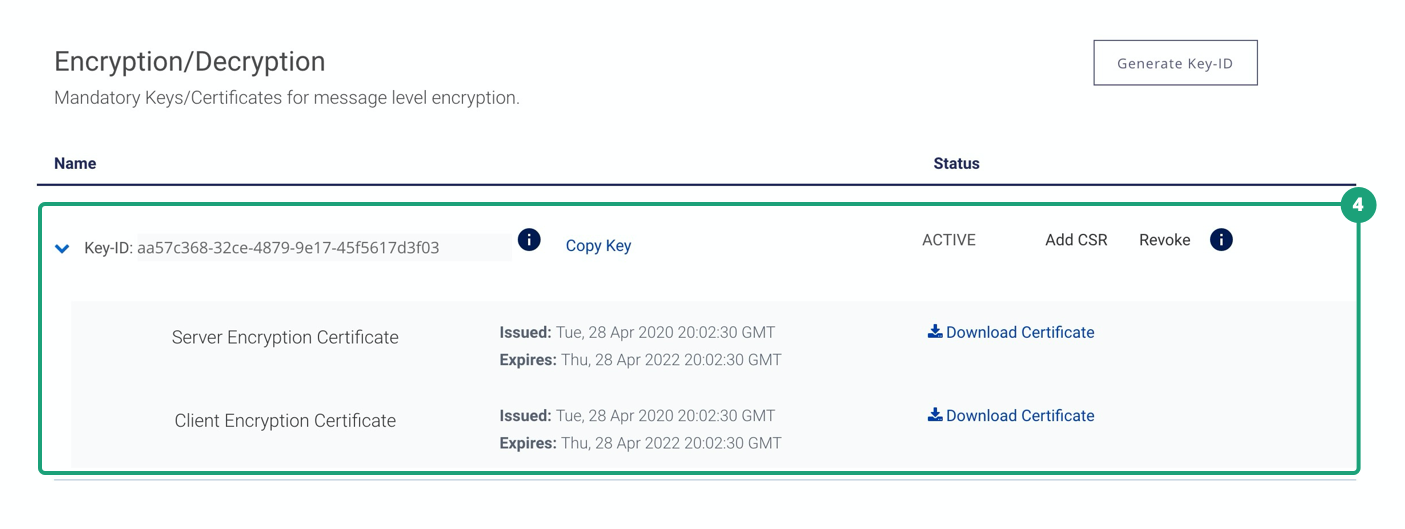
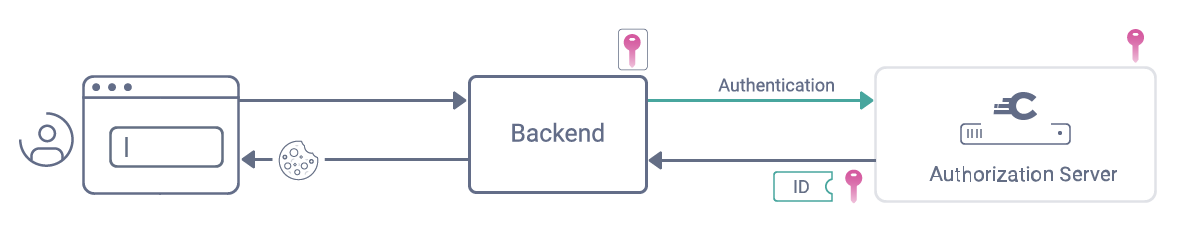
GitHub - aurasphere/jwe-token-decrypter: Simple command line util for decrypting JWE (JSON Web Encryption) tokens
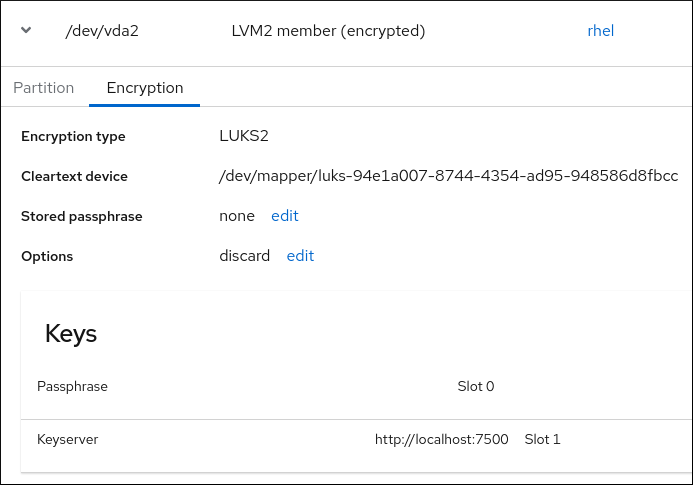
Chapter 11. Configuring automated unlocking of encrypted volumes using policy-based decryption Red Hat Enterprise Linux 8 | Red Hat Customer Portal